User tasks
Overview
This article shows how users manage their extra verification setup after their initial enrolment is completed. The examples and screenshots here assume Jira, but the user interface should be mostly identical on other applications.
Reviewing verification methods
Start by finding the Extra verification link in the user avatar menu in the top right corner:
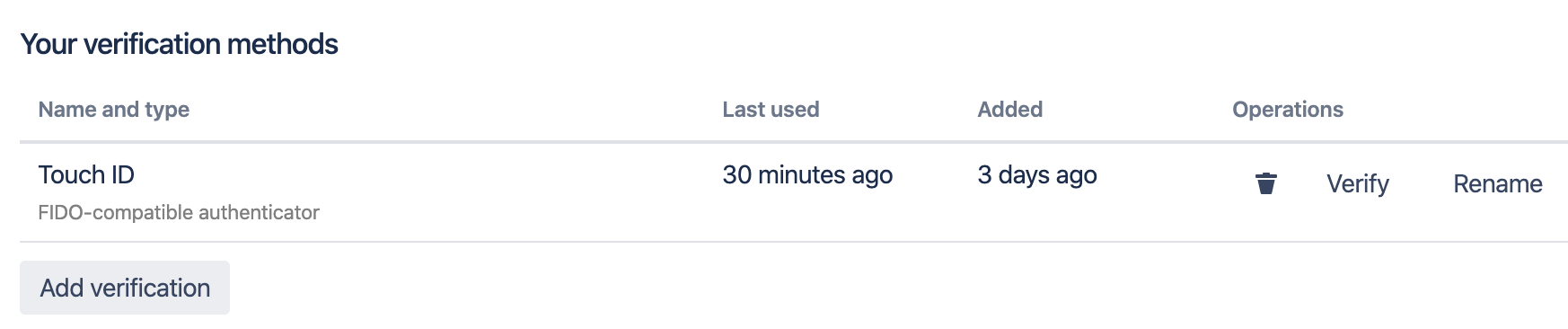
This page lists the user's current verification method. You can see when each verification method was last used, and the time of registration. Each verification method may be removed, tested or renamed.
Managing verification methods
It is recommended practice that users register more than one verification method. This allows other methods to be used if a security key is lost, a new computer is used or the user does not have access to their phone.
Click the Add verification button to register a new method. The steps for adding a method is already described in article registering for extra verification.
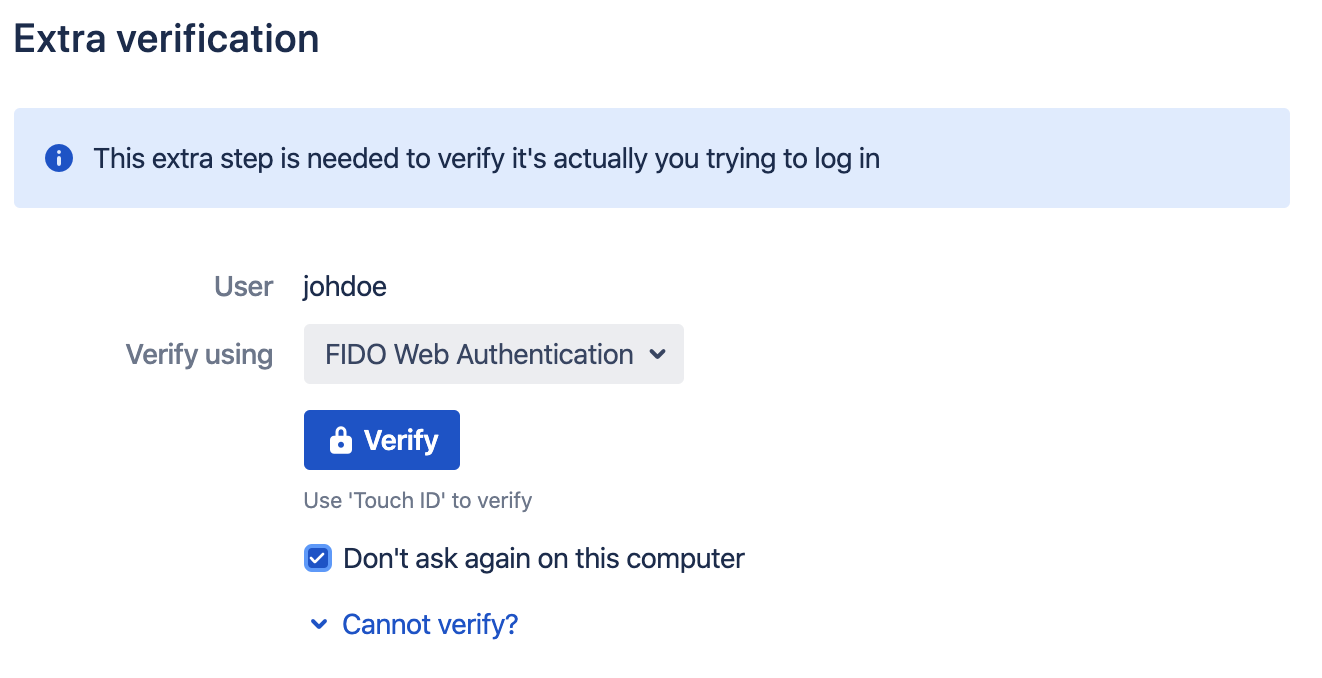
Testing
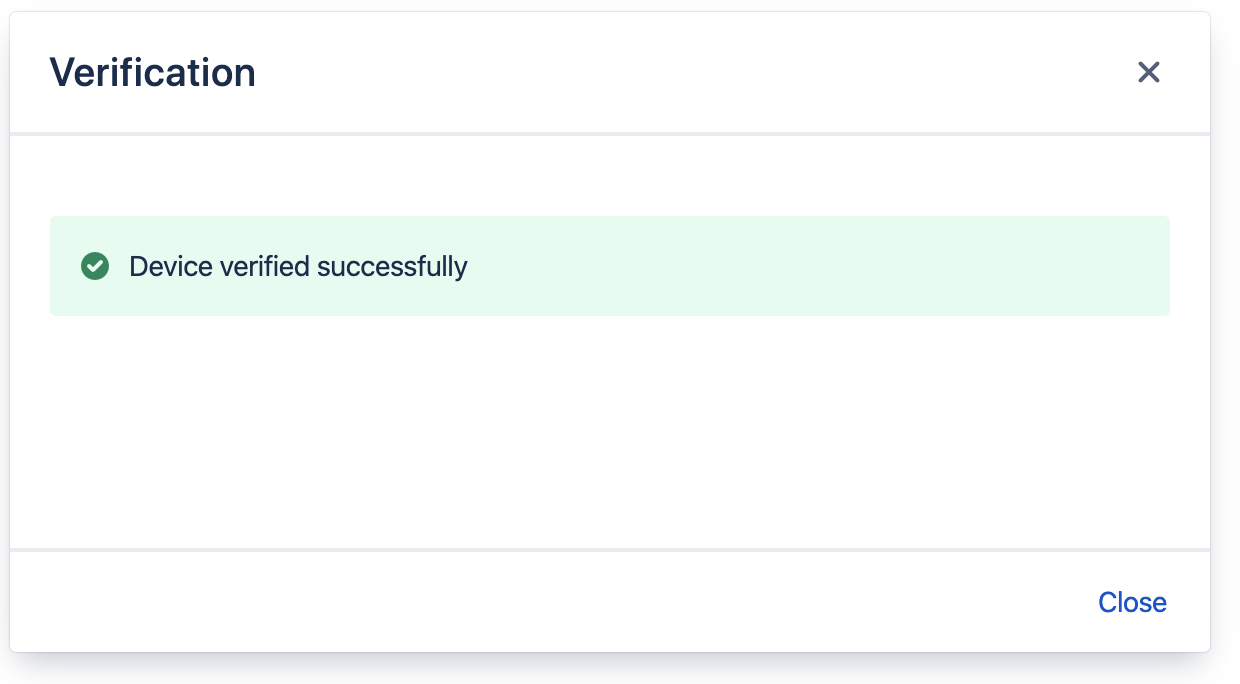
To test that you can verify using a registered method, click the Verify button.
Removing
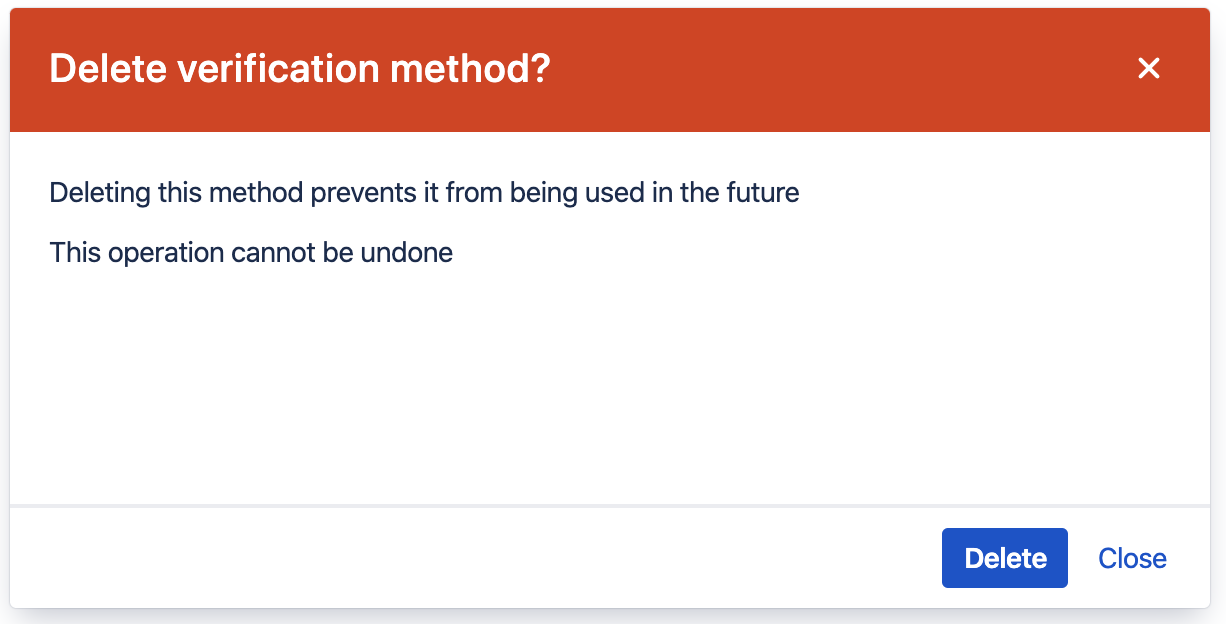
If a Windows Hello or Touch ID device is no longer in use, a security key is lost or a phone has been stolen, the user should remove the verification method to prevent it from being used by someone else. To remove a registered method, click the trash can button. A confirmation dialog will appear.
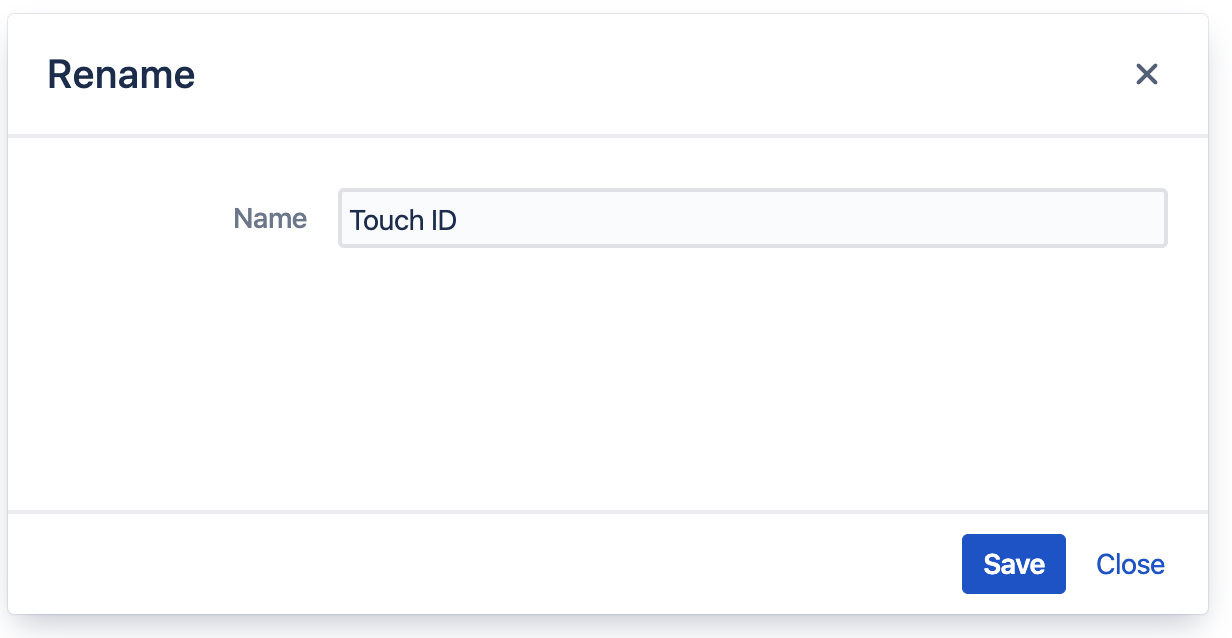
Renaming
If you are not happy with the name you have a verification method during registration, feel free to rename it. Click the Rename button and enter a name that better identifies the device.
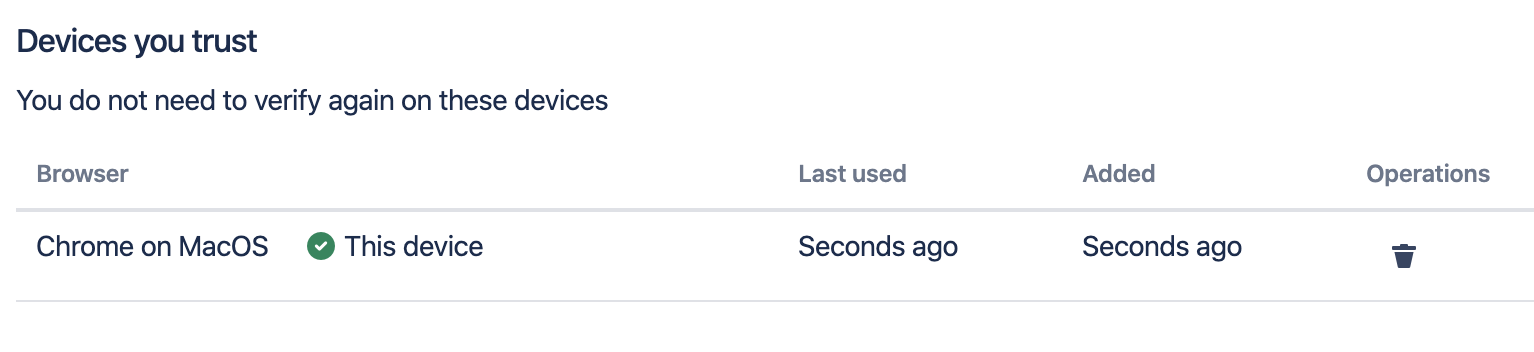
Trusted devices
Multifactor policies may allow users to remember extra verification on selected devices. This way, extra verification will only be required the first time a device is used.
A remembered device will appear in a list of devices you trust. If the device is later lost or stolen, you may want to remove it from this list. This ensures that anyone trying to get access from that device will need to verify again. If a trusted device is not used within 30 days, the user will need to verify again on that device.
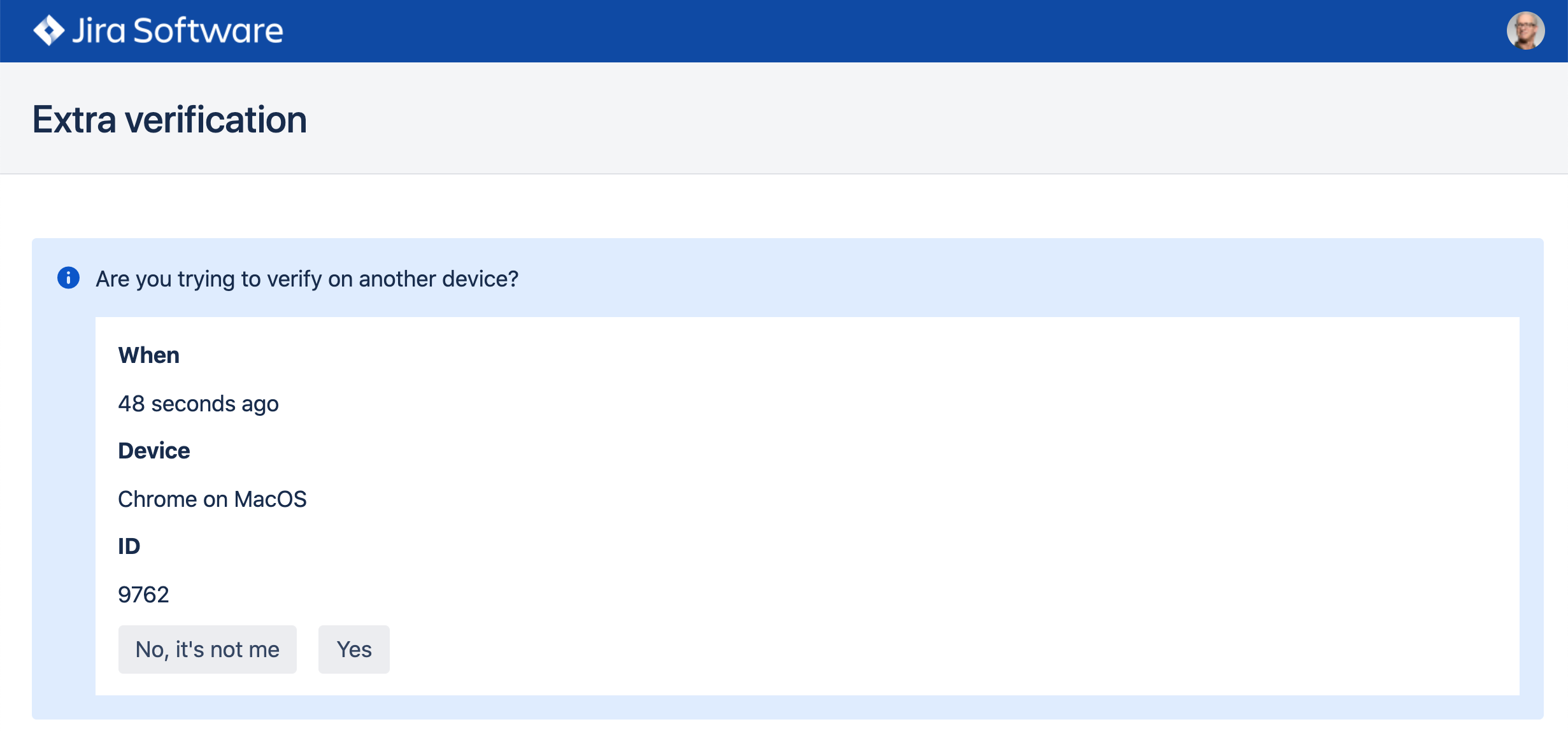
Pending verifications
Sometimes users find themselves in a situation where they have trouble verifying, or their authenticator is simply out of reach. The user may approve a verification request from a device where they are already logged in.